HTTPS administration
In WOCU-Monitoring we have enabled HTTPS for both the frontend and the communication between the backends.
The following are the operations to be taken into account.
Certificates
Three self-signed certificates have been created by default (by WOCU-monitoring):
Certified Authority
Private key:
wocuCA.keyCertificate:
wocuCA.pem
Aggregator
Private key:
wocu.keyCertificate:
wocu.pem
Import-tool
Private key:
wocu-it.key.Certificate:
wocu-it.pem
The above certificates are stored (for all flavours on the system) in: [/opt/wocu/embedded/ssl/certs].
WOCU-monitoring domains
By default, WOCU-monitoring is shipped with separate domains for the Aggregator and Import-tool.
For Aggregator domain is wocu (access
https://wocu)For the Import-tool, the domain is wocu-it (access
https://wocu-it).
DNS
The wocu and wocu-it domains will need to be able to translate it to the IP of the machine with WOCU-monitoring already installed. Since they are self-signed certificates, these domains will need to be added to a DNS, however, we will use the /etc/hosts file on the system.
The following entries shall be added to the /etc/hosts file:
AIO (incorpora Agregador + Import-tool)
WOCU_AIO_IP wocu
Attention
Putting in an AIO (Aggregator + Import-tool) with the same DNS is because Nginx will expose only one port and domain, so the Import-Tool will be serving on the same port as the Aggregator and it will be the PROXY PASS of Nginx that will make the difference in access.
Aggregator
WOCU_AGGREGATOR_IP wocu
Import-tool
WOCU_IMPORT-TOOL_IP wocu-it
Aggregator configuration (GUI)
The following configuration is for an AIO flavour of WOCU-Monitoring in the Import-tool.
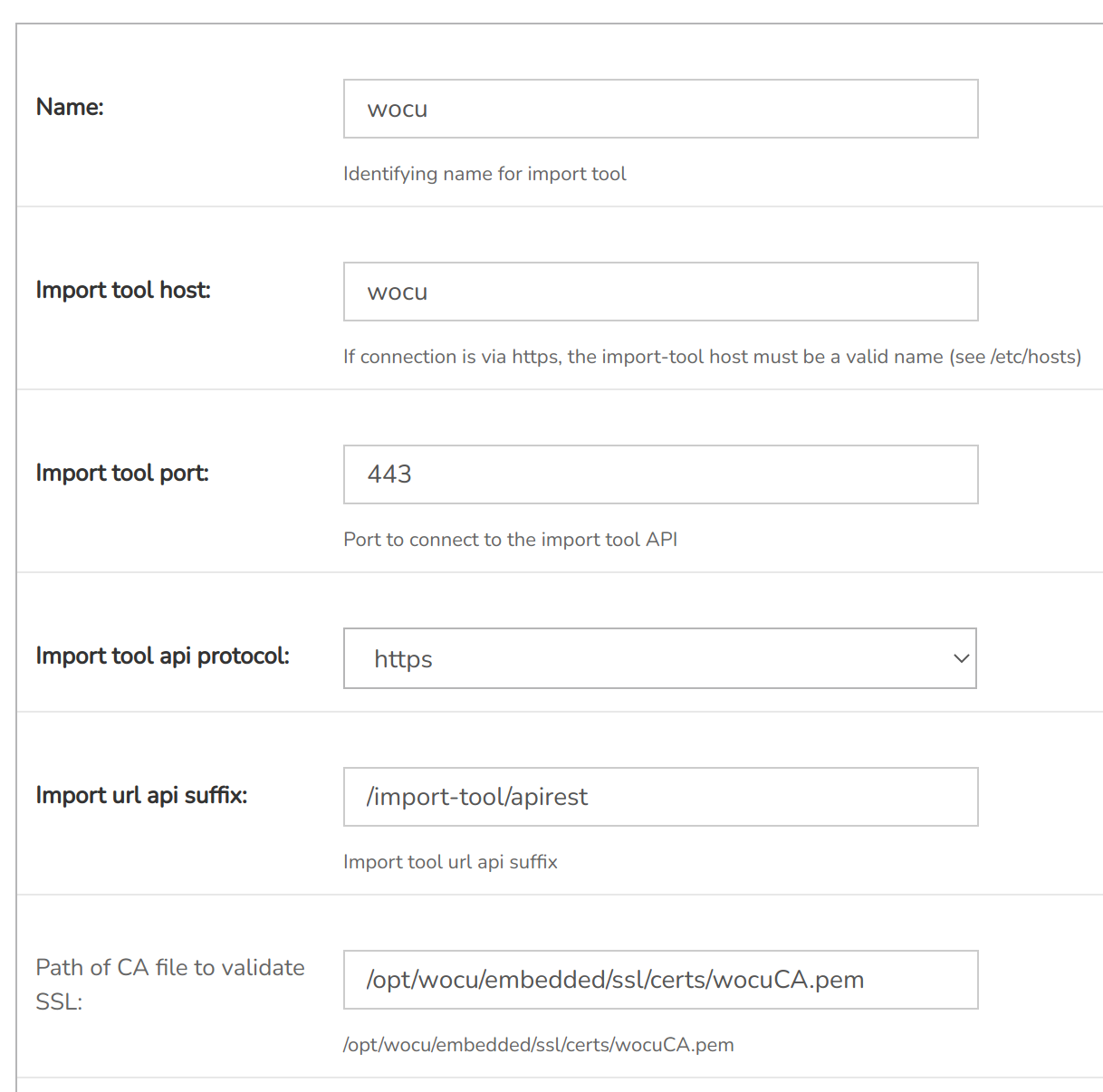
The following configuration is for a flavour monitoring from WOCU-Monitoring. In this case the Aggregator is not included.
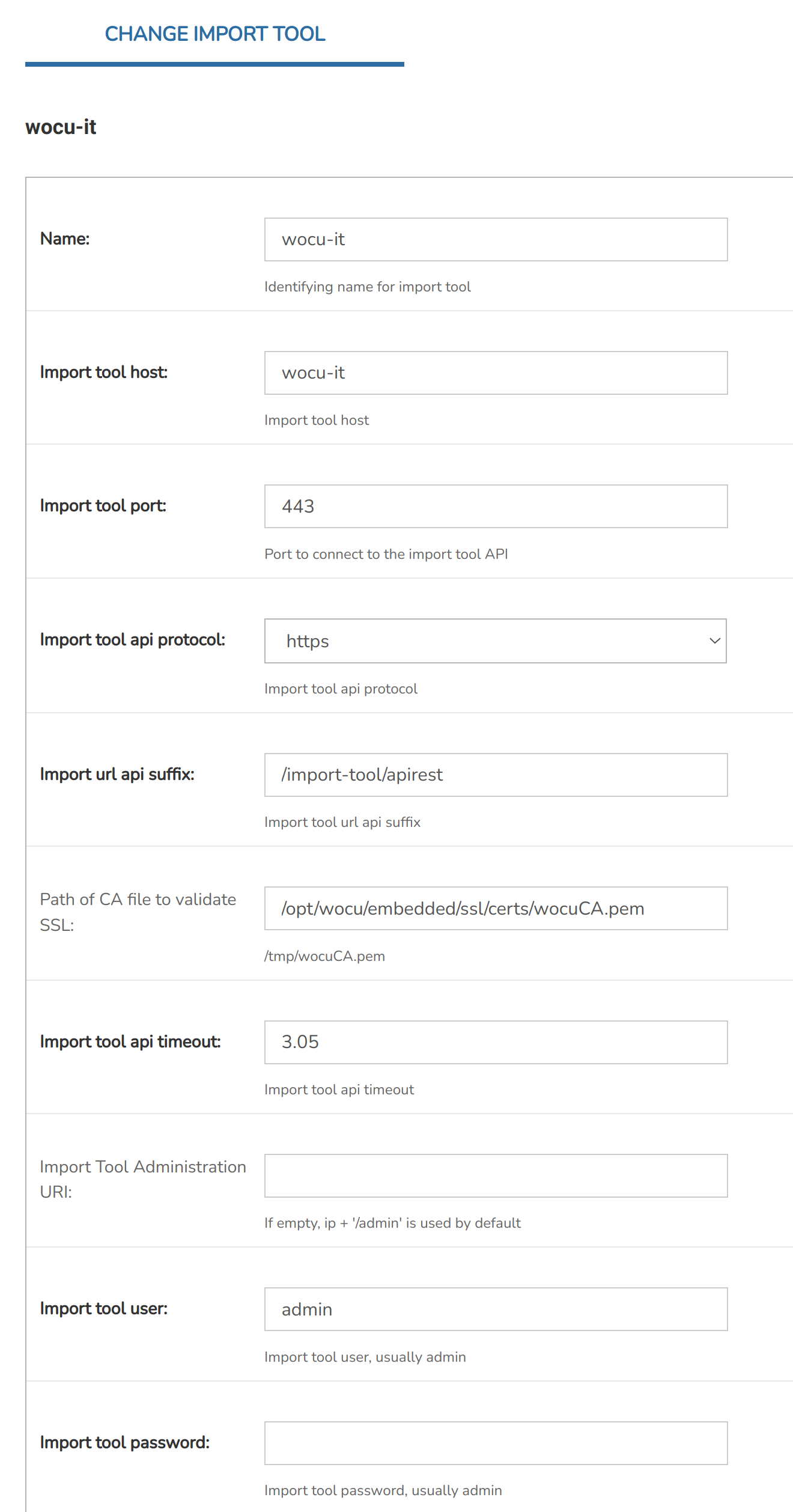
Guidelines and recommendations for parameter settings:
Import tool host: must match the name of the certificate.
2. Import tool port: must match the one configured in [
nginx/default] (default443).3. Import tool api protocol: in the use of certificates must be changed to https (default
HTTPS).4. Path of CA file to validate SSL: the path where the CA (Certificate Authority) of the Aggregator is stored must be entered. This certificate is used to verify the certificates of the added Import-tools (e.g.
https://wocu-it). In case of not adding the certificate path when HTTPS is enabled, the system will return a failure.
Generation of certificates
Since WOCU-Monitoring is deployed with only one certificate for the wocu domain (Aggregator) and for the wocu-it domain (Import-tool), in case there are more Import-tools, it will be necessary to generate a certificate for each of them.
To this end, the following tasks should be carried out:
An explanatory chart is set out below:
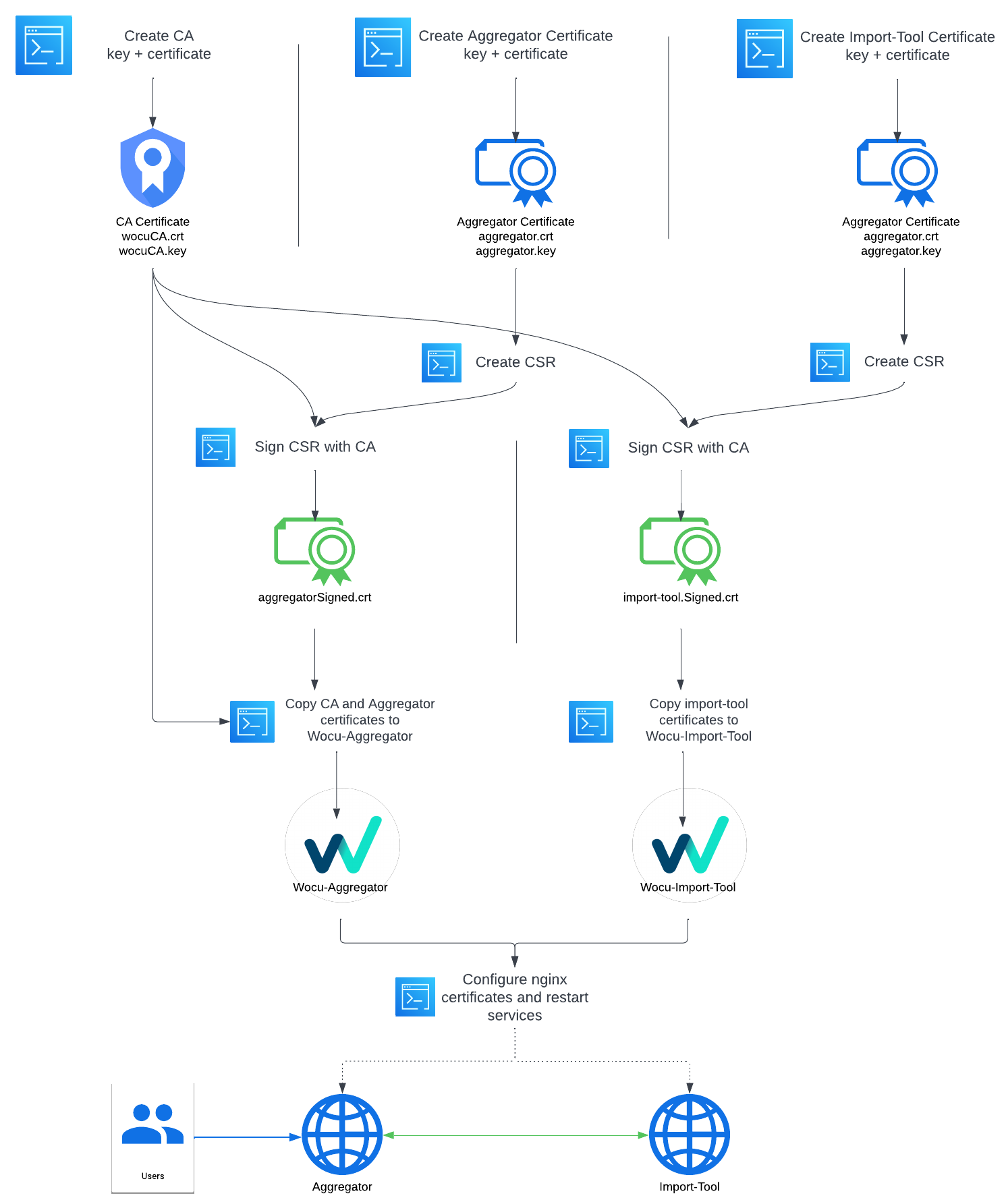
Generate certificates
For certificate generation we can use the CA already generated by WOCU-Monitoring, which we do not recommend unless it is a demo or similar case, so we will proceed to explain the complete flow.
This step must be repeated for each Import-tool and ultimately for the Aggregator.
Important
The path used to store the certificates must be accessible by the wocu user. That is why we will use by default
[/opt/wocu/embedded/ssl/certs].a. Creation of the key
For a CA, add
CAto the key name.openssl genrsa -out newCA.key 2048b. Creation of the certificate with the key.
For CA we use the key with
CA. For an expiry of less than 10 years, it will be necessary to change the value of-daysto the desired value.Important
When creating the CA and server certificates, the
CNmust not match between the two certificates as it will give aself signed certificateerror.openssl req -new -x509 -key newCA.key -out newCA.crt -days 3650When generating the CA or a new certificate (for Agregator or Import-tool) the following attributes need to be filled in.
C: Country
ST: State
L: Locality
O: Organization
OU: Organization Unit
CN: Common Name. It should be the same as the
$DOMAINexcept when creating a CA, which should be appended withCA.c. Creation of the file for the CSR (Certificate Signing Request).
cat > csr-$DOMAIN.conf << EOF [ req ] default_bits = 2048 prompt = no default_md = sha256 req_extensions = req_ext distinguished_name = dn [ dn ] C = ES ST = Madrid L = Madrid O = Wocu Monitoring S.L. OU = Wocu CN = $DOMAIN [ req_ext ] subjectAltName = @alt_names [ alt_names ] DNS.1 = $DOMAIN EOFImportant
You need to change the
$DOMAINvariable to the domain name and replace the variables associated with[ dn ].d. Creation of the CSR (does not apply to CA)
We proceed to generate the CSR using the
csr-$DOMAIN.conffile created earlier.openssl req -new -key new.key -config csr-$DOMAIN.conf -out new.csre. Creation of the .ext file to sign the CSR.
cat > $DOMAIN.ext << EOF authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment subjectAltName = @alt_names [alt_names] DNS.1 = $DOMAIN EOFImportant
Remember again to replace the
$DOMAINwith the domain.f. Signature of the CSR
openssl x509 -req -in new.csr -CA newCA.crt -CAkey newCA.key \ -CAcreateserial -out $CERTIFICATE_Signed.crt -days 1825 -sha256 -extfile \ $DOMAIN.ext
Modify Nginx
With the certificates already generated, the next step is to configure different Nginx parameters:
# # Certificates # server_name $DOMAIN; ssl_certificate $PATH/$CERTIFICATE_Signed.crt; ssl_certificate_key $PATH/$CERTIFICATE.key;
Again, we will change $DOMAIN to the name used in the certificates.
Modify Aggregator Import-tool
It will be necessary to modify the configuration of the Import-tool in the Aggregator as indicated in section Aggregator configuration (GUI).
Customer certificates
In this case, execute the tasks detailed in 2. and 3. of the Aggregator configuration (GUI).
Manten HTTP
In case you do not want to implement SSL between the Agregator and the Import-Tool you must keep the following configuration in Nginx.
In the server block, change the listen and server_name variables:
listen 80 default_server; server_name _;
Then comment on the variables of the certificates:
# # Certificates # #ssl_certificate $PATH/$NEW_CERTIFICATE.crt; #ssl_certificate_key $PATH/$NEW_CERTIFICATE.key;
Under location /import-tool:
#proxy_set_header X-Forwarded-Proto https;
Attention
In case of maintaining HTTP, no changes shall be made to the GUI of the Aggregator or Import-Tool.