Junk Assets
The Junk Assets list is another important area of the tool for the management of the monitored elements. It receives and temporarily hosts the assets imported after the execution of the CSV_Delete task. In this way, the user can evaluate and carry out the definitive deletion of particular assets from the monitoring plant.
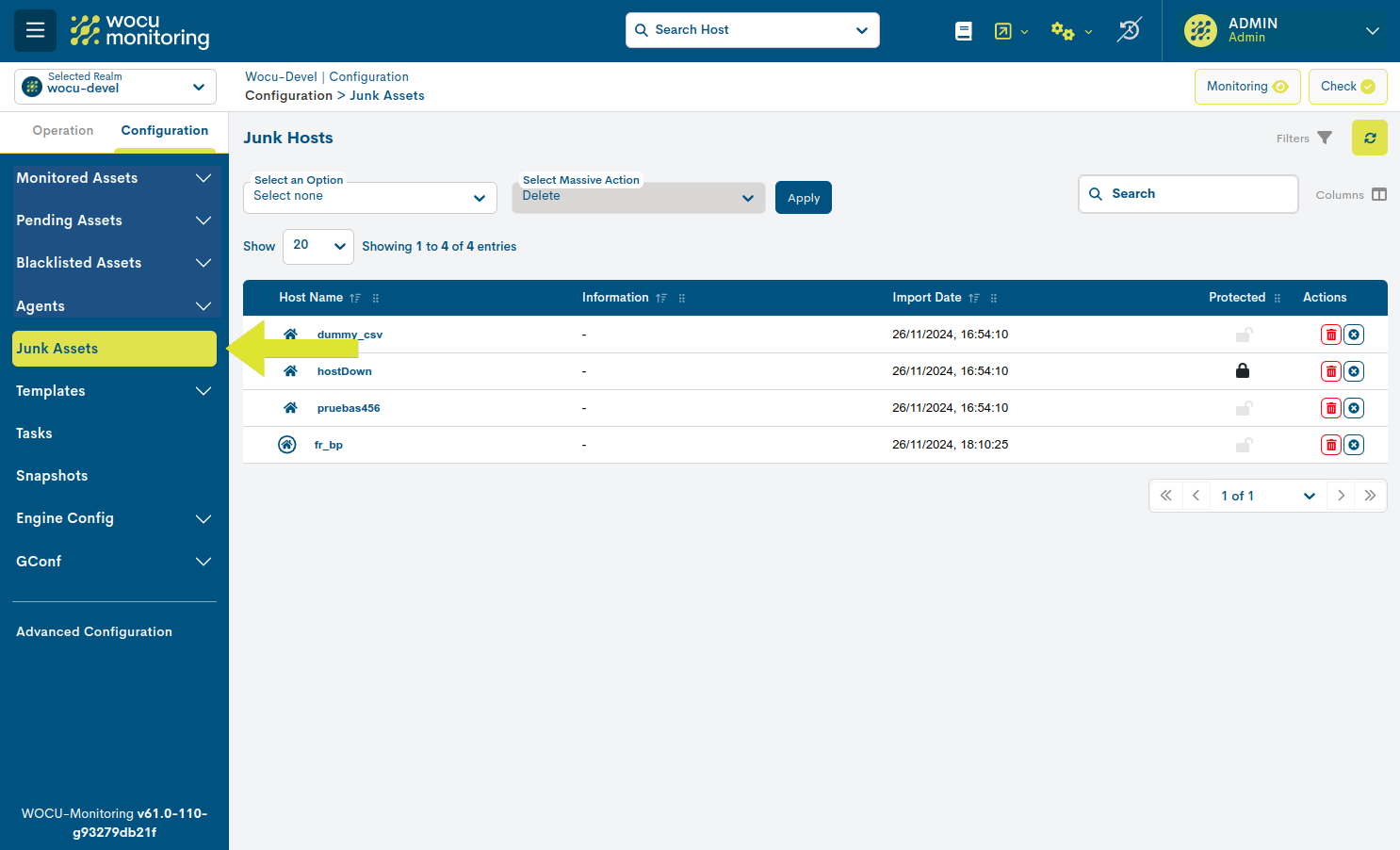
Junk or Scrapped Assets List Fields
The different fields/columns of the list are described below:
- ✓ Host name
Identificador del Dispositivo o Proceso de Negocio (Host Business Processes).
- ✓ Information
Annotation extracted from the CSV file imported by the operator in the CSV_Delete task. It is recommended to use this space to annotate any relevant information about the asset to be deleted that the operator considers appropriate to share with the rest of the users (Example: reason for asset deletion).
- ✓ Date of import (Import date)
The exact time at which the import of the asset takes place.
- ✓ Protected status
Depending on the nature of the asset, it may experience two possible states:
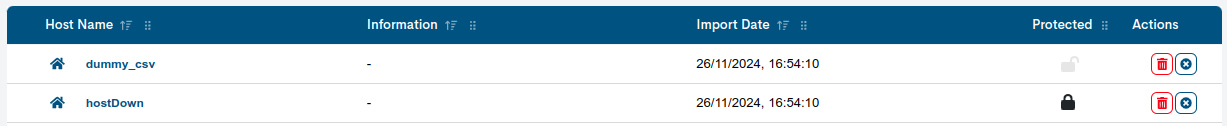
Protected: identified with the icon of a closed padlock (🔒). Indicates that the asset is locked, preventing to execute actions on it. This situation is caused by the linking of the asset to a Host Business Process or Service Business Process.
Unprotected: identified by an open padlock icon (🔓). Indicates that the asset is not locked and can therefore be deleted from the table or from the system.
Remember
The deletion of assets shall in no case leave orphaned elements. Assets linked to a Host Business Process or Service Business Process shall be locked in the table.
This exception does not apply to Host Groups, since the task will directly extract the element without altering any logical meeting (as it does in the case mentioned above).
Actions
The possible actions applicable to each entry in the table are described below:

Delete: proceeds to the definitive deletion of the asset from the monitored network (and from the list of Monitored Assets). The button will be locked (dimmed in colour), when the Host is protected due to its binding to a Business Process. More details in the Protected column and in the Information about dependencies (?) button.

Remove row: removes the asset from the table as it is not interested in being removed from the list of Monitored Assets.

Note
Massive deletion of table elements is also possible with the help of the Select all and Select an action selectors. See Massive_delete action for how this works.
Finally, any configuration done in this module requires the execution of the action Check to become effective.
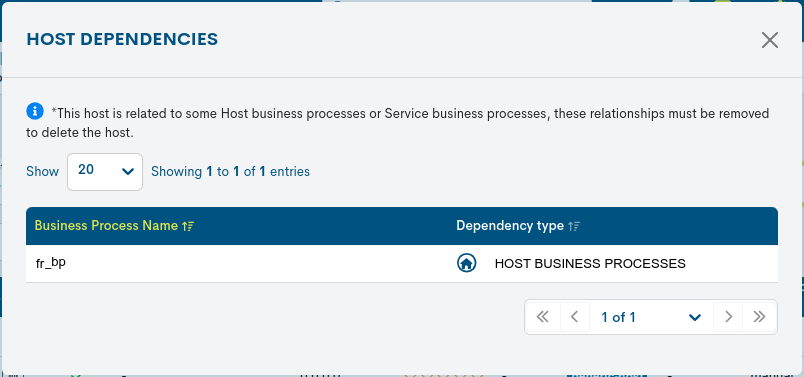
Information on dependencies
Clicking on the Protected icon (🔒) will display the Host Dependencies information window, which indicates the Host Business Processes or Service Business Processes of which the possible Host to be discarded is a part.
This correlation is the cause of its Protected status and, consequently, of the blocking of the deletion action (explained below).
The following data are displayed in a tabular format:
Business Process Name: name of the Business Process (logical entity) to which the Host is linked.
Dependency type: typology of the referenced logical entity. The possible options are:
Host Business Processes
Service Business Processes
Important
Until the user unlinks the Host from the Business Process, it cannot be removed from the system or the table as appropriate.
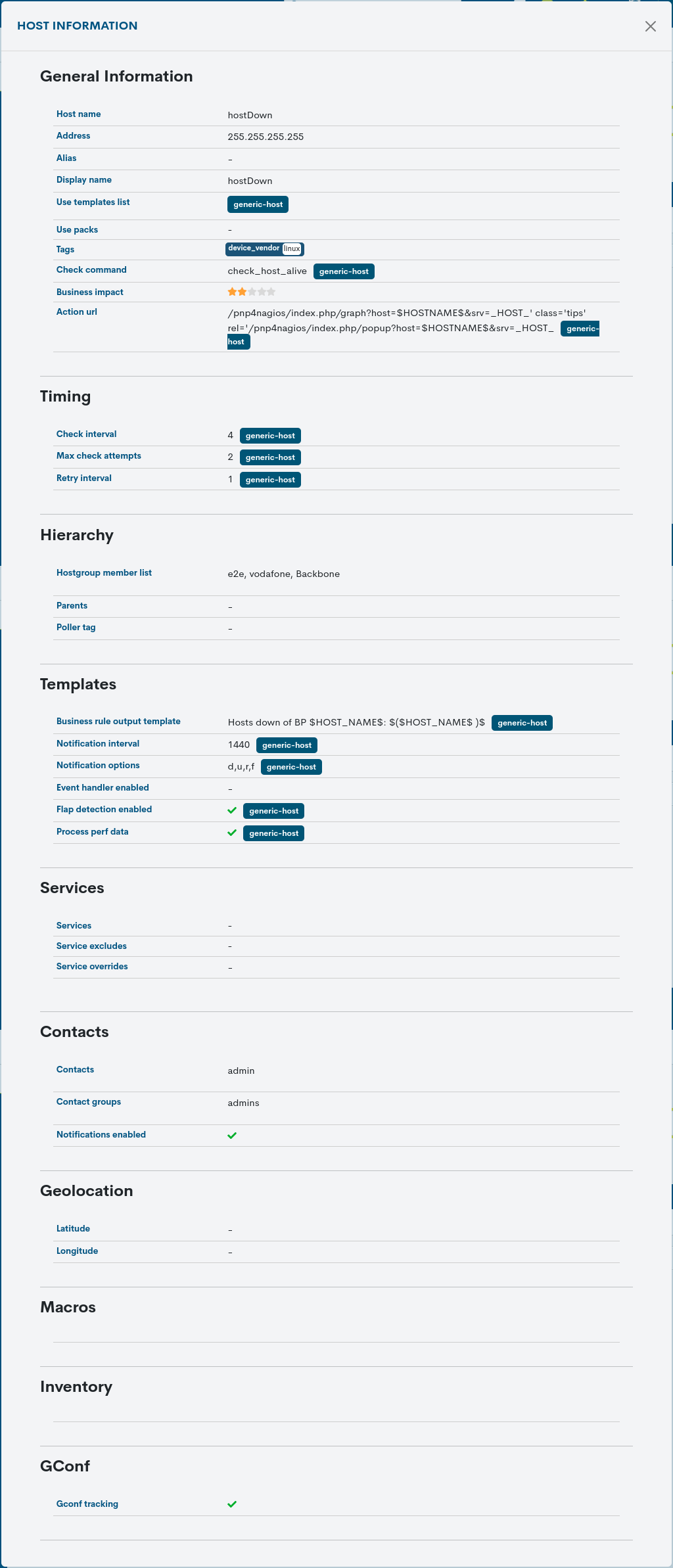
Detailed information on the device to be discarded
By clicking on the name of a particular item, the corresponding detail view will pop up with the configuration values of the different attributes of the Host registered in the system.
The user is referred to section Detailed Host Information, where these configuration attributes are described in detail.
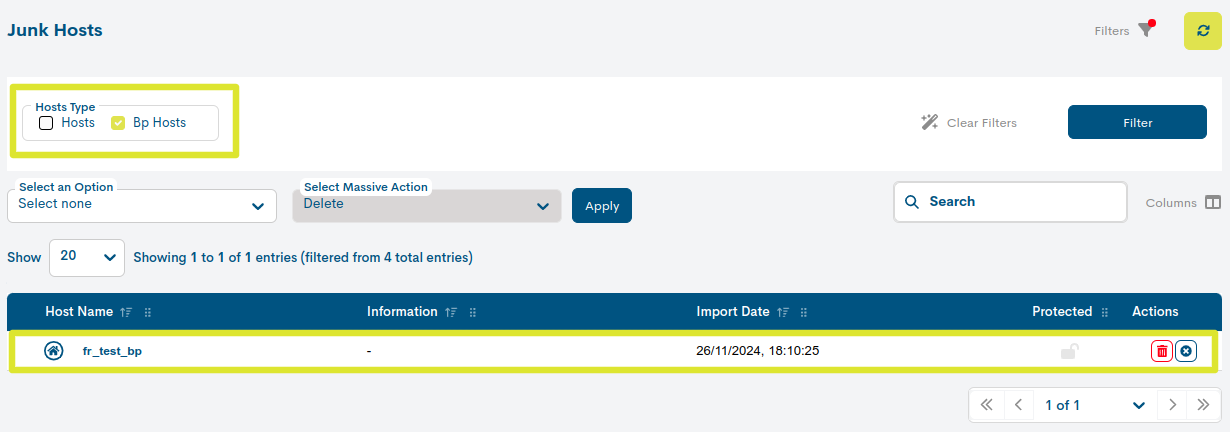
Filtering by type of Asset
This filter allows to distinguish the assets in the inventory by their typology, either Devices or Business Processes. This makes it much more agile when searching for specific elements in extensive lists.
Hosts are identified with the icon of a house.
Business Process Hosts (BP Host), i.e. logical devices, are identified by the icon of the house framed in a circle.
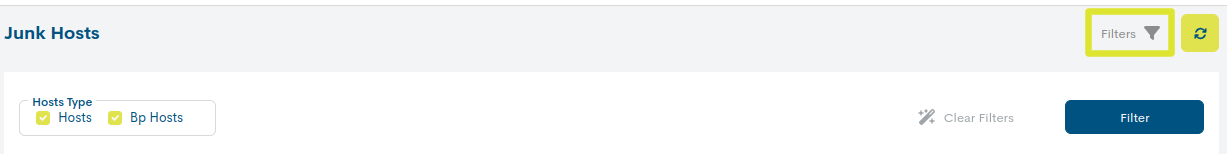
Su funcionamiento es muy sencillo, al seleccionar/deselecionar una o ambas opciones el listado será actualizado de forma inmediata mostrando o excluyendo los ítems en cuestión.